World Smallest Passive Ethernet Tap
Hello folks!
This is my first English blog post. Excuse me for my hopefully not so bad English 😊.
During my reverse engineering on the Terratec Noxon 2 Audio I had to sniff the network traffic between the Noxon and the Internet. First, I just sniffed the wireless traffic with a simple ARP spoofing attack in my switched network. But I couldn’t be sure whether I sniffed the whole traffic or if I just missed some internal traffic in my network.
After some internet research, I decided to build my own passive Ethernet tap to do a MITM (man-in-the-middle) attack.
Snort and Geekslunch have excellent instructions for this. Diego Gonzalez Gomez also published a very nice paper about receive only UTP cables. I strongly recommend to read these documents before building your own tap.
Note that you can only receive data from the connection. Injection is impossible with a passive tap!
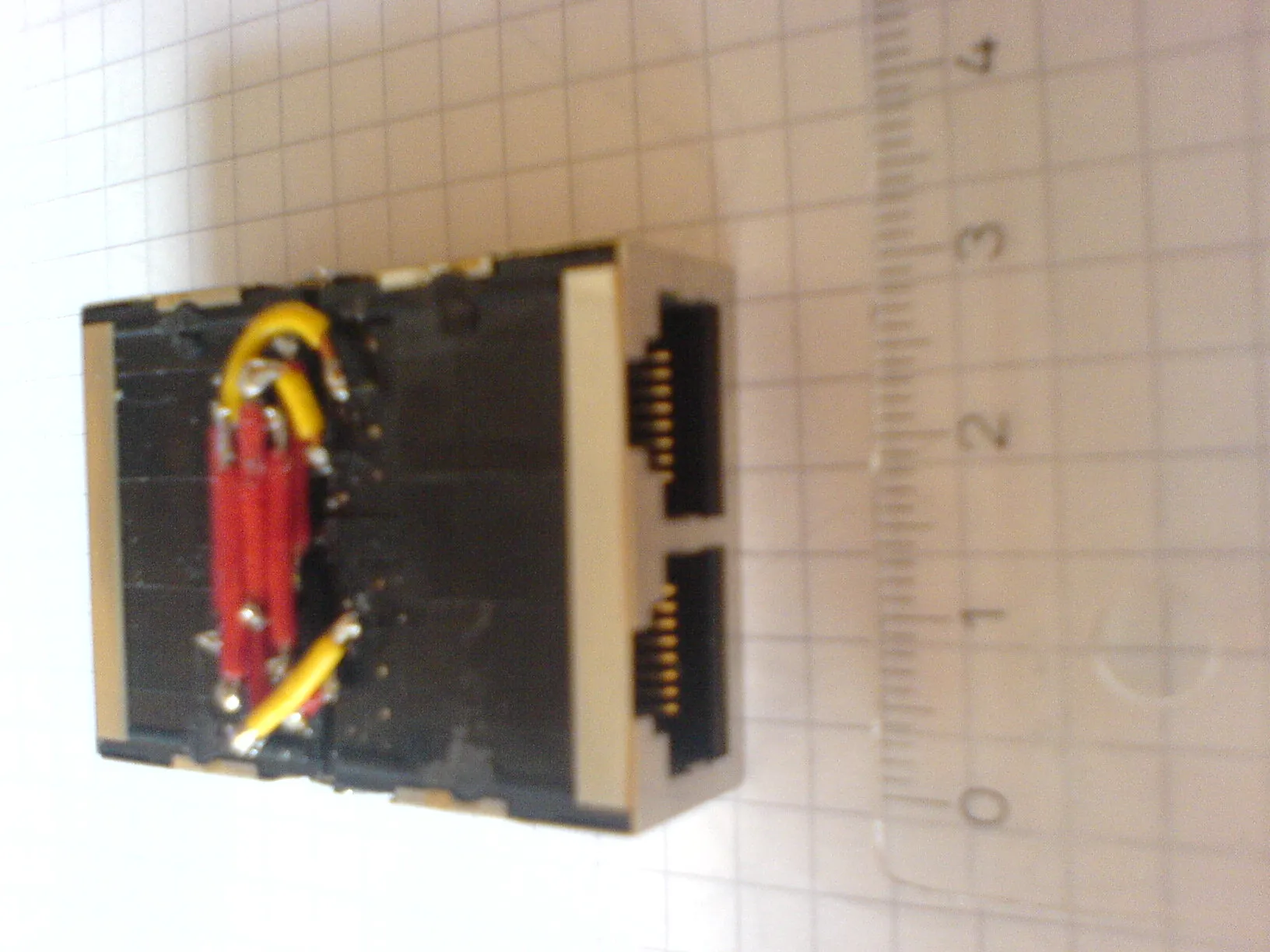
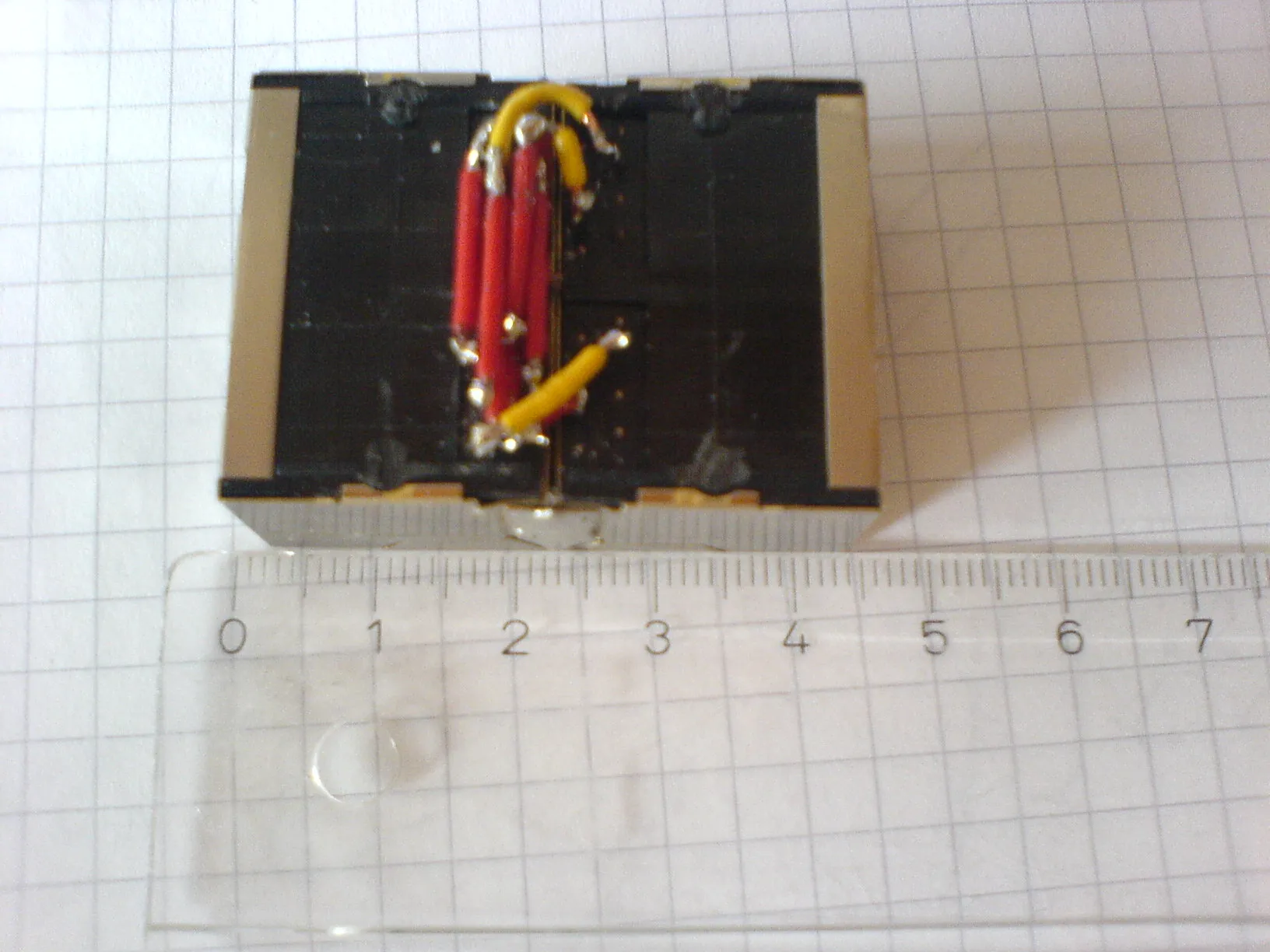
If you want do modify or inject packets you should use two network interfaces as a bridge. For my tap I used two screened two-port RJ-45 connectors which I soldered together.
Finally here some pictures of my tap. It’s the smallest I found on the internet! It has a size of 431 cm!




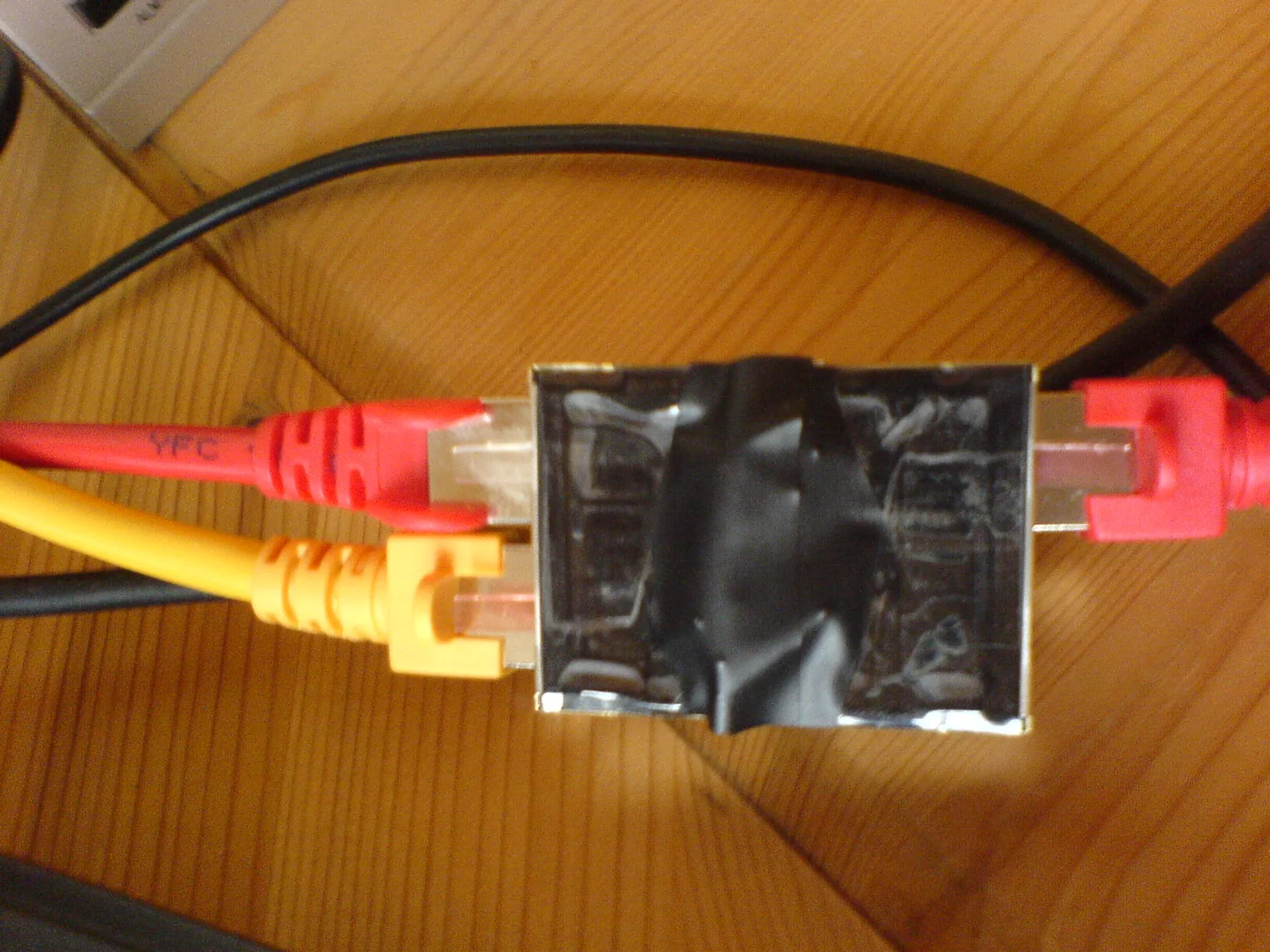
Lastly, a small tip for sniffing both directions simultaneously.
For this you need two NICs.
Link them together with the bonding Kernel module.
Here is a little How To and some documentation.